APQ IPC Manager
Platform based operation and maintenance, application integration, and centralized equipment operation and maintenance management
Monitoring the health status of equipment and preventing faults instead of repairing them
Analyze operation and maintenance data to form a dynamic knowledge base
Multi platform compatibility: Windows, Linux, Android
- Condition Monitoring
- Equipment Debugging
- Data Backup
- Remote Control
- Abnormal Event Reporting
- Batch Maintenance
-
Supervise
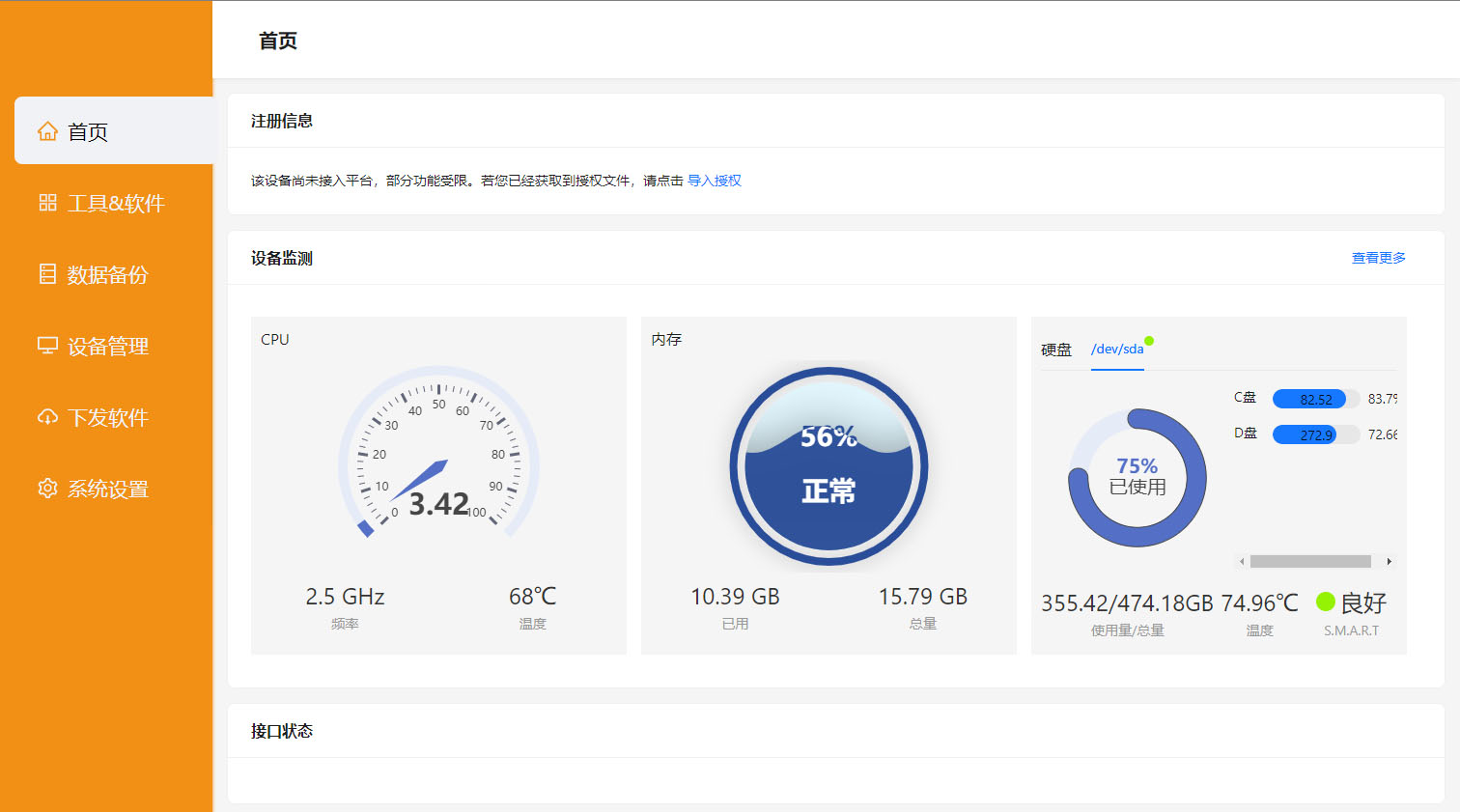
Real Time Monitoring
Remote real-time monitoring of equipment
Historical Data Tracing
Tracing of equipment historical data and operation and maintenance data
Device Alarm Notification
Equipment anomaly warning
Mobile Maintenance
Mobile APP
-
Supervise
Real Time Monitoring
Remote real-time monitoring of equipment
Historical Data Tracing
Tracing of equipment historical data and operation and maintenance data
Device Alarm Notification
Equipment anomaly warning
Mobile Maintenance
Mobile APP
-
Supervise
Real Time Monitoring
Remote real-time monitoring of equipment
Historical Data Tracing
Tracing of equipment historical data and operation and maintenance data
Device Alarm Notification
Equipment anomaly warning
Mobile Maintenance
Mobile APP
-
Supervise
Real Time Monitoring
Remote real-time monitoring of equipment
Historical Data Tracing
Tracing of equipment historical data and operation and maintenance data
Device Alarm Notification
Equipment anomaly warning
Mobile Maintenance
Mobile APP
Software Architecture
Apply SaaS Layer
APQ Operation and maintenance system
- Equipment monitoring
- Efficiency analysis
- Data modeling
- Product Traceability
- Cost Analysis
- Equipment monitoring
- Efficiency analysis
- Data modeling
- Product Traceability
- Cost Analysis
Platform Layer
APQ IoT platform
- Device authentication
- Device access
- Equipment monitoring
- Equipment management
- Application management
- Cloud API
- IT Operation Management
- Lifecycle management
- Object Model Definition
- Rule engine
- Firmware update
- ......
Network Transport Layer


APQ Edge Gateway
Internet / 2G / 3G / 4G / 5G, NB-loT
Network Transport Layer












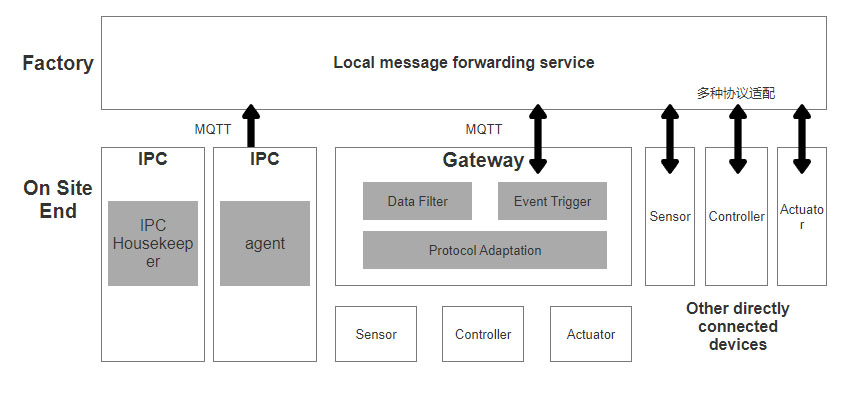
Supports two methods of cloud deployment and local deployment

In order to simplify network deployment configuration, additional local message forwarding services will be deployed within each subnet of the project site.
On the IPC deployed by the visual analysis system of each machine on site, deploy the Agent to complete the IPC's own control execution and attribute event collection.
Optional software gateway for protocol adaptation, private API conversion, and access to various sub devices.